Version: 1.38.2.0
Frequency: Consistently
Severity: High
Context: Aircraft utilizing our endpoints via WASM
Bug description:
Using the WASM network API, simple GET requests to our CDN fail for certain users. The exact same request works fine in Coherent using fetch. Our best working theory is that it is related to the user’s certificate trust store on their computer.
For a bit of context - this fall, AWS stopped supporting the Starfield C2 CA for any new certificates. When we renewed our certificates, requests started failing in MSFS 2020. We tracked down this change and decided to attempt to use a different certificate - and we decided to go with Let’s Encrypt. As soon as we switched the certificate out, things started working again.
Now, the issue has returned (it’s also possible the issue was present back then, but we just didn’t get any bug reports for it). Since we don’t have enough insight to tell what is causing the network requests, we’d like some help here if possible. All we can see at the moment is that the request returns a negative response code, indicating a network error.
For debug purposes, here is a sample URL.
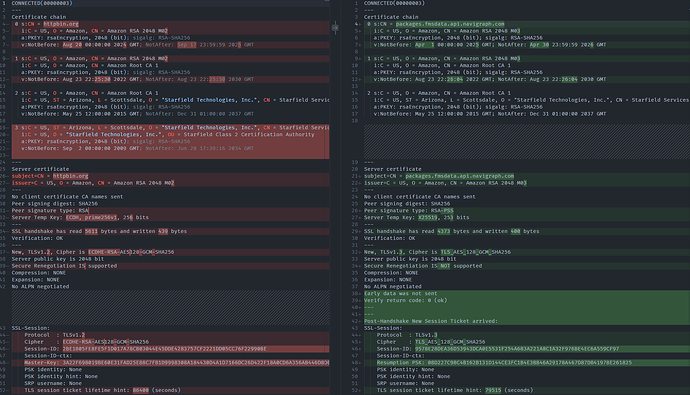
And here is our certificate chain
1. End-entity certificate (Level 0):
- Subject: CN=packages.fmsdata.api.navigraph.com
- Issuer: C=US, O=Let's Encrypt, CN=E6
- Key: ECDSA, 256-bit
- Valid until: Apr 9 13:40:13 2025 GMT
2. Intermediate CA (Level 1):
- Subject: C=US, O=Let's Encrypt, CN=E6
- Issuer: C=US, O=Internet Security Research Group, CN=ISRG Root X1
- Key: ECDSA, 384-bit
- Valid until: Mar 12 23:59:59 2027 GMT
3. Root CA (Level 2):
- ISRG Root X1
- C=US, O=Internet Security Research Group, CN=ISRG Root X1
It is interesting to note that the issue is not present at all on 2024 - likely due to changes in the underlying implementation of the network API.
We understand an update to 2020 is very unlikely anytime soon, so any insight into what could be going wrong and how we can fix it on our end would be greatly appreciated.
Repro steps:
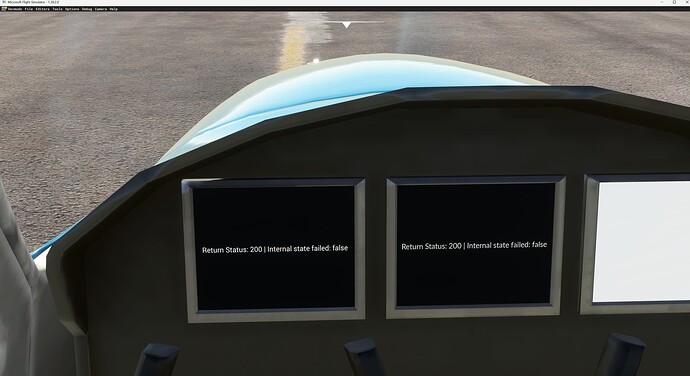
Reproducing is very inconsistent; as stated above, this only affects certain users. For those users who are affected, reproducing is as simple as spawning onto the runway with the aircraft attached. The leftmost gauge is WASM, and the one to the right is a JS gauge.
Attachments:
Minimal reproduction aircraft with source: NetworkAircraft.zip - Google Drive
Screenshot from a user without the issue:
Screenshot from a user with the issue: